Cyber security for plant operators INNOVATION WELCOME – A SURE THING!


AT A GLANCE:
Cyber security for your plant technology –
ask us!
ask us!
- We understand complex OT systems as a whole in order to reliably assess the impact of errors and establish mitigation mechanisms. Our experience shows that a comprehensive combination of system, software, and security expertise is essential. For many of our customers, this defines the “Codewerk factor.”
- We operate and maintain your security monitoring system on the basis of Security Onion. This helps you reliably detect attacks both from within the network and from hosts.
Codewerk services for
secure plant management:
- Insecure standard configuration:A quick and easy target for hackers, but still a widespread one. This is where our fuzzing comes in – a deliberate attempt to crash the system with randomly generated input data. Based on the insights obtained, we then apply our software expertise to optimize the source code.
- Code vulnerabilities:Most software is sourced externally – and is therefore beyond the control of the product manufacturer. Our continuous vulnerability monitoring and management reveals security loopholes – in libraries or frameworks, for example – and assesses their potential repercussions.
- Insecure data validation and input checking:If inputs are not properly validated, hackers can inject malicious code (e.g. SQL injection or cross-site scripting) into the system and execute it. Using Security by Design, we counter this risk right at the development and testing phase.
System-, Software- and Security-Know-how
To embed security comprehensively, you need to understand complex systems like process control technology or train control systems in detail.
Timon Esslinger, Cyber security expert at Codewerk



The product is ready – how about a little security on top?
Why Security by Design in accordance with IEEE 62443 pays off
Which security monitoring solution must I use?
Points in favor of Open Source



See also:
“Head in the sand” no longer applies
Standards-compliant cyber security for your OT –
ask us!
ask us!
THE CODE TO YOUR SUCCESSCodewerk
- A decade of experience as an independent software developer and service provider
- Four locations in Germany
- Partner in national and international R&D projects and in the open Siemens Xcelerator ecosystem
- Certification to ISO Standard 27001 since 2020
Model-based software engineering for the vehicle control unit
GETTING THERE FASTER
We speed up the development and validation of vehicle control software using model-based software engineering.
DEVELOPMENT OF IOT AND EDGE APPLICATIONS
FOR SMART RAIL OPERATIONS
By monitoring “health states,” identifying optimization potentials in the network, and enabling predictive maintenance, our application development transforms your data into knowledge.
Subsystem integration for the vehicle control unit and operator network
SO IT ALL WORKS TOGETHER
When subsystem integration is performed for the vehicle control unit and operator network, we take full responsibility for combining multivendor architectures to form a functioning whole.
Innovations
WE’RE SHAPING THE FUTURE
We play an active role in both national and international research projects that are working to prepare rail vehicle technology for the challenges of future decades.
Development of a basic system
BASIS FOR THE FUTURE
By participating in international standardization projects, we’re contributing to the creation of a highly expandable and modular basic system of the future.
Device integration for SIMATIC PCS 7 / SIMATIC PCS neo
YOUR COMPONENTS IN A LEADING POSITION
Siemens’ SIMATIC PCS 7 and SIMATIC PCS neo control systems are leaders in the process industry. We take responsibility for a seamless, system-compliant integration of your products or third-party components.
PROFINET Stack Integration
WE HELP YOU MAKE IT TO THE BIG LEAGUES
You want to integrate PROFINET into your chips or devices – we handle the modification of the relevant stacks as part of a carefree package for you – right up to certification.
System integration for industrial communication
SO THAT NO DATA-POINT IS LOST
Whether it’s PROFINET, OPC UA, MQTT, or applications based on them, we take on the complete integration of products for industrial communication into your system environment.
Development of IoT and edge applications
DATA BECOMES THE BASIS FOR DECISION-MAKING
You want to turn big data into smart data. We’ll build your application – from data acquisition (connectivity) and data transmission to data evaluation and utilization.
IO-LINK LIBRARY FOR SIMATIC PCS 7/SIMATIC PCS NEO
Secure point-to-point connections in industry are relatively easy to implement with the right IO-Links. We offer you the right driver so that integration is in full compliance with the system.
TURCK Remote IO FOR SIMATIC PCS 7
The system-compliant connection of TURCK systems to the SIMATIC PCS 7 process control system doesn’t have to be time-consuming. Our function block library ensures maximum convenience at the user end.
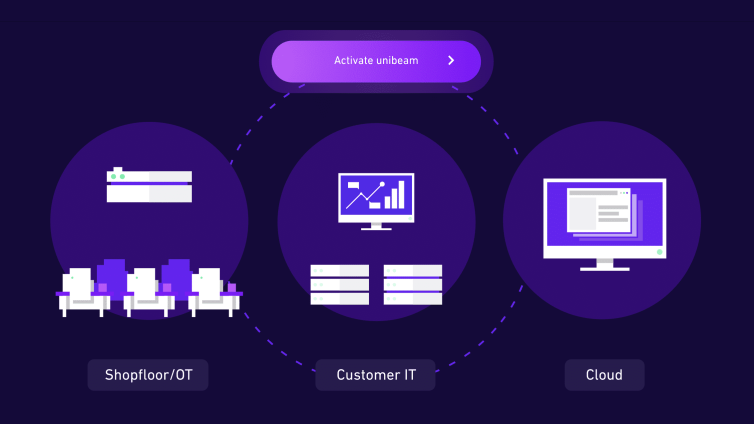
unibeam. - And suddenly it's all Smart Factory.
Do you want to experience a new generation of IIoT-platforms? Discover unibeam: an amazingly simple and efficient software to help SMEs unfold their whole potential of digitalisation.
Cyber security for component manufacturers
SECURE FROM THE START
How we help you eliminate potential vulnerabilities in your products – from product development throughout the entire lifecycle.
Cyber security for plant operators:
MORE PROTECTION FOR YOUR ASSETS
How we can help you monitor and mitigate risks during operation – supported by our combination of system, software, and security expertise.